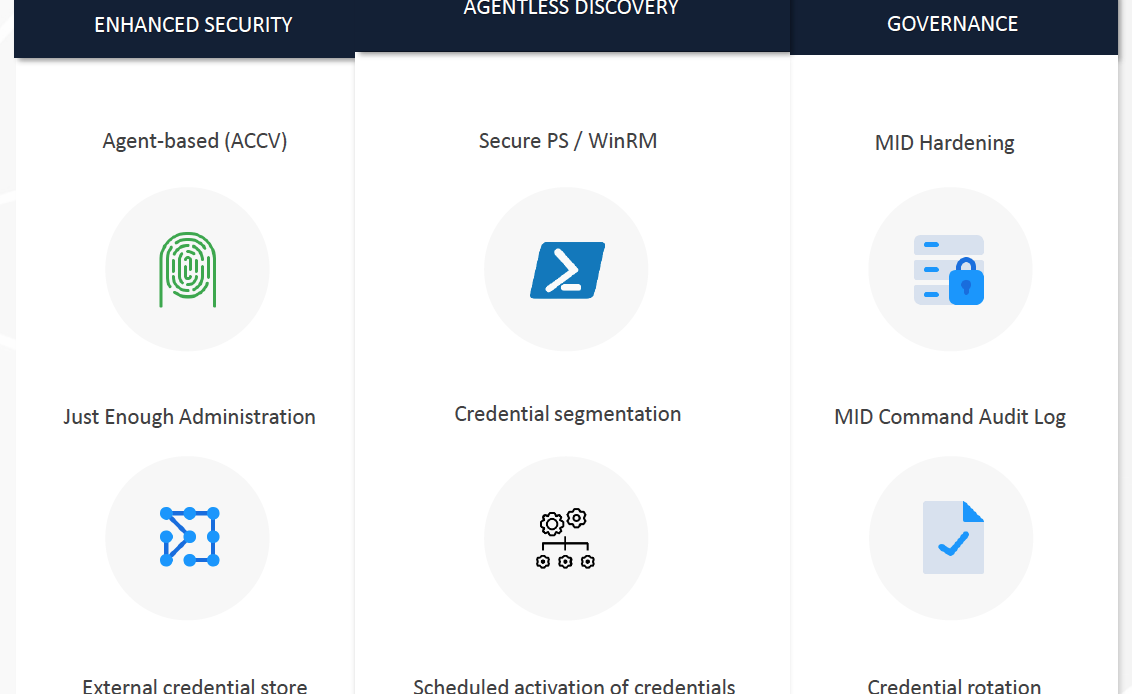
Creating a secure discovery implementation is not always easy. There is always a balance between what is practical and secure. In this infographic, we have summarized some of the key-areas that are important for a security discovery implementation.
Enhanced security
For enhanced security, consider the following areas.
Agent based discovery for sensitive network
The world of discovery is not black or white. You might have parts of the network that are more sensitive than others. This is especially common if you work in an industry which have to follow certain audits and compliance rules (such as pharma, health-care, manufacturing etc). For some parts of the network, having an agentless discovery and uploading credentials is simply not an option. If that is the case – consider the agentbased discovery as an alternative.
Just enough administration
Tired of providing local administrator rights when you do Discovery? Then you are not alone. Consider JEA (Just enough administration) to discover windows machines. This is a PAM solution developed by Microsoft, and has been in the platform quite a while.
External credential store
Did you know you can easily integrate with CyberArk and ServiceNow? Did you know you can build your own, offline credential store? The possibilities are many to connect external credentials from another source to ServiceNow. Just be aware of the impact on discovery rollout- & implementation.
Agentless Discovery Security Tips
To improve the agentless (traditional) discovery and it security, follow these simple areas.
Secure PS / WinRM
Don’t rely on WMI when there is secure powershell & WinRM. WMI have many security concerns and should only be used for older windows devices where WinRM & Secure Powershell is not supported.
Credential Segmentation
Segment the credentials based on IP-blocks, domains or subnets. To have a solid strategy for where credentials are valid and under what circumstances is key to a secure agentless discovery.
Scheduled Activation of Credentials
For those environments that needs to be very secure, it is possible to create methodologies where credentials are only valid during certain time windows. Any other time-window and the credentials are deactivated/made inactive. Note that there is no possibility to do this from ServiceNow, but you would need to create or buy a solution that facilitates this type of automation (credential rotation).
Governance for Discovery
Half the battle won is having good processes. Such as:
- MID Hardening – make sure your MID-servers are hardened, patched and restrict access to only specific users. You can also consider security solution such as CarbonBlack.
- MID Command Audit Log – This is a tool where you exactly can audit and see what commands have been executed on the MID-servers, built in directly in ServiceNow
- Credential Rotation – Rotate the credential frequently to enhance security
Much can be said about securing discovery, and it is one of the most important factors in a Discovery project. Hopefully this article gives you some inspiration of what can be done.
Download High Resolution Infographic (For FREE)